Types of Substitution Ciphers
In my previous post, I defined substitution ciphers, and how to decrypt them through frequency analysis. In this post, I will discuss various substitution ciphers that were used throughout history.
One substitution cipher simply uses a random permutation of the letters of the alphabet as the key; this was the example I used in the previous post. While this type of cipher is very secure, it is also inefficient for both the sender and the receiver to have to coordinate a long, random key which was sometimes even longer than the message itself.
One of the most simple and well-known substitution ciphers was the Caesar shift. This cipher took every letter of the original alphabet and shifted it by a certain value. For example, if the value was 2, the cipher alphabet would be:
A->C
B->D
C->E
All the way up to Y->A and Z->B.
This was more efficient than a random key because the sender and receiver only have to know one number, instead of a whole alphabet. However, it was easy to crack, because the enemy only had to try 26 different keys, or even better, only had to perform frequency analysis with one letter. The Caesar shift was also one of the first ciphers to be usable through machines like the Caesar wheel.
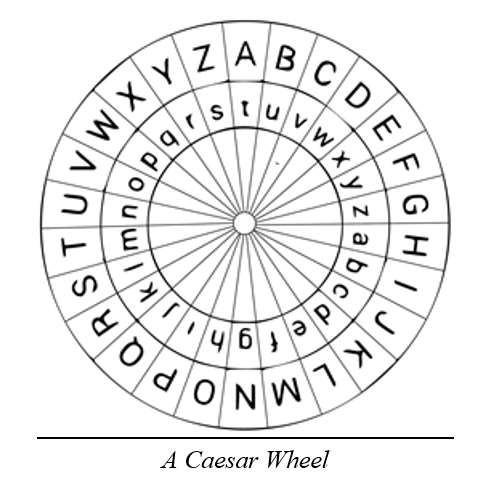
Another more efficient version of substitution was the key cipher. This cipher made use of a word that both parties knew to generate the key. For example, if the key was LEMON, the cipher alphabet would look like this:
ABCDEFGHIJKLMNOPQRSTUVWXYZ
LEMONABCDFGHIJKPQRSTUVWXYZ
In the case of a word with repeating letters, the repeating letters were removed. For example, GOOGOLPLEX would look like this:\
ABCDEFGHIJKLMNOPQRSTUVWXYZ
GOLPEXABCDFHIJKMNQRSTUVWYZ
This provided a balance between efficiency and security, as it wasn’t as inefficient as a random key, but more secure than a Caesar shift.